AWS SAM: Authorization Middleware using token-based Lambda authorizer
A token-based Lambda authorizer is an API Gateway feature that uses a Lambda function to control access to the public APIs.
AWS SAMAWS LAMBDAAPI GATEWAY
2 min read
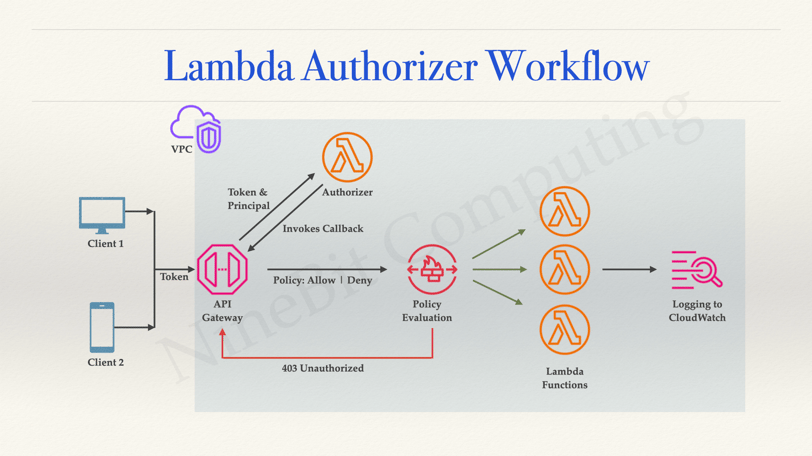
Step 1: Lambda as an Authorizer
The first step in this journey is to create a Lambda function that will act as an Authorizer for accessing APIs. Internally, it can also invoke Authentication workflow but that is beyond the scope of this article. You can create a Lambda Function either using AWS Console or using CFT. Since this article is dealing with SAM topics, we recommend to declare the Lambda Function as a resource in your CFT.
Cloud Formation Template details:
Declare a new "AWS::Serverless::Function" in CFT and name it as "AuthLambda"
Provide its Handler and VPC properties
"Events" properties should omitted
Node.js Handler details:
In this step, the Authorization handler extracts the token from request header as shown below and fires an existing API to validate it. Based on the response received it invokes the callback with an appropriate IAM Policy document.
What is AWS SAM?
AWS SAM is a framework that allows you to build a stack of serverless applications on AWS. It provides a simplified way to define, package, and deploy serverless applications using AWS CloudFormation (IAC).
Step 2: Create Authorizer in API Gateway
API Gateway provides a range of features that allows you to secure your APIs and control access to your serverless functions. In this step we will link the Lambda Authorizer that we created in the previous step with the API Gateway with the help of a new Authorizer in AWS Console.
Navigate to API Gateway and open Authorizers section to create a new Authorizer
Choose Lambda as Authorizer type and select the Lambda Function created in the previous step
Select token-based payload and provide a name to request header that will bear the token
Test the Authorizer by passing some random token. View the logs in CloudWatch for this CFT stack
Step 3: Add authorization middle-ware
The final step is to wire up the components together to build a safety net for your Lambda Serverless Functions so that only authorized users or entities will be able to access your function.
Under API Gateway, navigate to Resources and select the method that you want to secure
Edit method request settings and choose token based authorizer that we created in the previous step
Ensure that http request header is pre populated with the header name that you provided earlier
Save the settings
Test the setup
In order to test the step up, we will require the public endpoint of the API Gateway and a API client tool. Lets use Postman for that purpose.
Navigate to API Settings of API Gateway
Copy the default endpoint and append the stage name (e.g. prod) at the end of the endpoint
Use Postman and prepare the request with the URL and the request header
Use CloudWatch to view the logs
Remember to always follow best practices for securing your serverless applications and regularly review and update your authorization settings to ensure the highest level of security.
